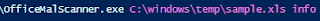
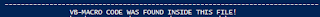
SUBJECT: RECONFIRM INVOICE
ATTACHMENT: RECONFIRM INVOICE.doc
The code was interesting because it seemed amateurish in terms of it's obfuscation. Sure there were tons of random looking letters, variable names, etc. But in general, this was poorly obfuscated, if at all. Here are a few examples:
Private Const HHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHighMask
The above variable was used for doing bitwise masking of a string value, yet the attacker literally named it "HighMask" so you know exactly what it's used for.
Public Function Encode64(sString As String) As String
The above function literally performs base64 encoding of a string, so the name Encode64 makes sense and makes life simpler for the security researcher.
Public Sub Wipedir(pppppppppppppppppppppppppp As String)
The above function Wipredir calls the VBA deletefolder method in it, so again it's clearly deleting the evidence afterwards, thus the obfuscation here is poor.
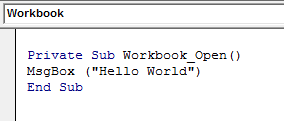
So de-obfuscating this was quite simple then. One of the easier ways to quickly de-obfuscate VBA code like this is to put it into a word document, comment out the malicious lines, replace them with MsgBox statements, and execute the code, let the code do the work for you. For example:
Comment out this code with a tick
'MkDir (decryptString(Encode64(b)))
And replace it with this code
MsgBox ("MkDir=" + decryptString(Encode64(b)))
Comment out this code with a tick
'ChDrive (vEnd988888527)
And replace it with this code
MsgBox ("ChDrive=" + vEnd988888527)
Comment out this code with a tick
'Open vEnd3491963883 For Binary As vEnd1400215006
And replace it with this code
MsgBox ("OpenFile=" + vEnd3491963883)
Comment out this code with a tick
' OBsGG = Shell(vbHH, 1)
And replace it with this code
MsgBox ("Shell=" + vbHH)
Comment out this code with a tick
'OOO.deletefolder pppppppppppppppppppppppppp
And replace it with this code
MsgBox ("deletefolder=" + pppppppppppppppppppppppppp)
And like magic, you'll get a bunch of message boxes that tell you exactly what this code is trying to do. In this case
1.) Create a new folder C:\ProgramData\Memsys
2.) Navigate to that folder C:\ProgramData\Memsys
3.) Open and Write to a file C:\ProgramData\Memsys\ms.exe
4.) Execute that file from the command prompt C:\ProgramData\Memsys\ms.exe
5.) Delete that folder C:\ProgramData\Memsys
Of course always do this in a sandbox, not connected to the Internet, in case you accidentally execute malicious code that you didn't mean to and infect yourself.
More about neonprimetime
Top Blogs of all-time
- pagerank botnet sql injection walk-thru
- DOM XSS 101 Walk-Through
- An Invoice email and a Hot mess of Java
Top Github Contributions
Copyright © 2016, this post cannot be reproduced or retransmitted in any form without reference to the original post.