Have you been digging deep into your IDS logs and noticed this snort alert ever?
FTPP_FTP_BOUNCE (125:8)
alert (msg:"FTPP_FTP_BOUNCE"; sid:8; gid:125; rev:1; metadata:rule-type preproc, service ftp; classtype:bad-unknown; reference:cve,1999-0017; reference:url,www.kb.cert.org/vuls/id/276653; )
Let's try to figure out what it means. So I opened my packet capture and saw 2 records.
X1.X2.X3.X4:18663 => Y1.Y2.Y3.Y4:21 [ FTP , COMMAND=PORT, ARGS=Z1,Z2,Z3,Z4,P1,P2 ]
X1.X2.X3.X4:42762 => Y1.Y2.Y3.Y4:21 [ FTP , COMMAND=PORT, ARGS=Y1,Y2,Y3,Y4,P3,P4 ]
The source IP X1.X2.X3.X4 was a Post NAT address where a lot of traffic goes through. The destination IP Y1.Y2.Y3.Y4 was some externally hosted FTP server. But those FTP commands looked a bit weird so I had to google what they meant. This old article about the FTP port command tells me that Z1,Z2,Z3,Z4 actually is listing the client's ip address Z1.Z2.Z3.Z4! And P1,P2 is a hex formatted version of the Client's Port. Same thing then for Y1,Y2,Y3,Y4 and P3,P4.
So what the Snort rule is trying to tell you is that the Source IP is sending 2 FTP PORT requests, but the Client IPs provided in the PORT command don't the match the real client's IP.
This flaw is old and most modern FTP servers handle this scenario by validating that the Source IP and the IP provided by the client match the original ones given, but it's interesting to see an alert on it anyways.
Conclusion: This was a false positive. Why? Because IDS didn't know that this was a Post NAT IP address (basically every user inside a company is seen to the outside world has coming from 1 IP address from your company). And thus the IDS didn't know that this really wasn't the same user, it was 2 different users hidden behind the NAT. Thus this situation requires some tuning in your IDS or SIEM monitoring tools to ignore.
Keep monitoring those logs!
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Showing posts with label FTP. Show all posts
Showing posts with label FTP. Show all posts
Friday, March 13, 2015
Wednesday, January 7, 2015
Password Sniffing Insecure Protocols is Too Easy
I suggested previously that we should just bite the bullet and kill insecure protocols like HTTP. Sometimes it's difficult to take a statement like that seriously unless you see what the malicious actors can do first hand. Thus for demonstration purposes only I'm going to show you a simple little tool that anybody (both good guys & bad guys) can get for free.
Please keep in mind my intent of this post is to hammer home the point that we should kill HTTP and other insecure protocols like FTP, etc. So, let's say I have a legit reason to look for passwords on my system. Perhaps I forgot my password, but you know some application on my system is using the password, then I can recover it with this tool. Keep in mind, it's not a far stretch at all for a malicious user to perform very similar tasks with illegitimate intentions.
The tool we're taking 2 minutes to look at is SniffPass – Simple Password Sniffer. You could start by reading darknet's article and downloading SniffPass. Please note if you're running an Anti-Virus like McAfee it may detect SniffPass.exe and delete the downloaded file as Tool-PassView, or PUP (potentially unwanted program)
Once downloaded and extracted, double-click on SniffPass.exe to open it up.
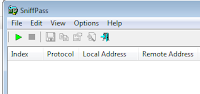
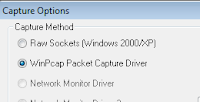
Next, click the green start arrow. Then select any of the options you have (RawSockets, WinPCap, etc.). For this demonstration they all work.
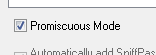
Something of interest, notice there is a Promiscious Mode checkbox you could utilize. Wow, I wonder if that might come in handy for somebody? :-P
After you hit ok, you're basically done. Your final step is to activate the application using the insecure protocol (perhaps you have filezilla running already with your saved password, perhaps you goto an FTP site in your browser, perhaps a website that requires basic windows authentication, etc.) Run the application or type in your username & password that you thought was perhaps secure. Find out immediately per the screenshot below that you're not.
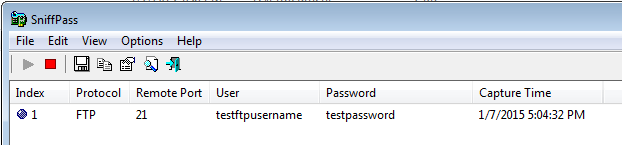
The sad part? This was too simple. It took me literally 2 minutes from download to successful usage with a tool I had never in my life used before. Is it time to get rid of those insecure protocols yet? I think so.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Please keep in mind my intent of this post is to hammer home the point that we should kill HTTP and other insecure protocols like FTP, etc. So, let's say I have a legit reason to look for passwords on my system. Perhaps I forgot my password, but you know some application on my system is using the password, then I can recover it with this tool. Keep in mind, it's not a far stretch at all for a malicious user to perform very similar tasks with illegitimate intentions.
The tool we're taking 2 minutes to look at is SniffPass – Simple Password Sniffer. You could start by reading darknet's article and downloading SniffPass. Please note if you're running an Anti-Virus like McAfee it may detect SniffPass.exe and delete the downloaded file as Tool-PassView, or PUP (potentially unwanted program)

Once downloaded and extracted, double-click on SniffPass.exe to open it up.

Next, click the green start arrow. Then select any of the options you have (RawSockets, WinPCap, etc.). For this demonstration they all work.

Something of interest, notice there is a Promiscious Mode checkbox you could utilize. Wow, I wonder if that might come in handy for somebody? :-P

After you hit ok, you're basically done. Your final step is to activate the application using the insecure protocol (perhaps you have filezilla running already with your saved password, perhaps you goto an FTP site in your browser, perhaps a website that requires basic windows authentication, etc.) Run the application or type in your username & password that you thought was perhaps secure. Find out immediately per the screenshot below that you're not.

The sad part? This was too simple. It took me literally 2 minutes from download to successful usage with a tool I had never in my life used before. Is it time to get rid of those insecure protocols yet? I think so.
Copyright © 2015, this post cannot be reproduced or retransmitted in any form without reference to the original post.
Subscribe to:
Posts (Atom)