Just a heads up I'm moving all my PhishingKitTracker blog posts ( @PhishKitTracker - https://github.com/neonprimetime/PhishingKitTracker ) over to this new blog url
https://phishingkittracker.blogspot.com/
This blog ( @neonprimetime ) will continue to be for #malware and other #infosec topics
Showing posts with label Phishing Kit. Show all posts
Showing posts with label Phishing Kit. Show all posts
Friday, May 10, 2019
New PhishingKitTracker Blog
Tuesday, May 7, 2019
IzLaden - Phishing Kit Author
#izladen #phishingkit author #threatactoremail izladen-Free-Tools@hotmail.com ---- | ★ ★ ★ IzlAden BenGazi FREE TOOLS ★ ★ ★ | ---- |----------| IzlAden BenGazi V3 TEXT RESULT |--------------| Coded By IzlAden BenGazi ===> 2016 / 2017 227ce240dff32a0a35810b0040539ae2 https://www.virustotal.com/#/file/735a16f31af8159af71c40738a22c5638d41bd58144014b9a3fee00390a1da6b/details a9fd8300c7a5654f1ee9247ebdb3e42a https://www.virustotal.com/#/file/7434db52972fd2aa7f253bded2efff92f6069fd9e8ff7beb27c5d998ce803c41/detection c37d8e468a67748c7f9687ecfe39c960 https://www.virustotal.com/#/file/4e1ce76c96c3163d1da5060157b4c0924647e4938843f827f36380837bb7610e/detection
FudPages - Phishing Kit Author
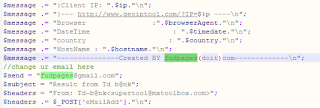
#fudpages #phishingkit author #threatactoremail fudpages@gmail.com ---------------Created BY fudpages(doit)com------------- ---------------Created BY fudpages------------- ----------- FUDPAGES [.] RU -------------- abc845784335374ecb86cc7d9f105ba7 https://www.virustotal.com/#/file/3e76cff314a6b4fef91784f8fab3f21e985f68bd9aa909cdca0245611a3f8757/detection 070a0ebacac551e86ed00e1118f9a969 https://www.virustotal.com/#/file/bcb77cbee636b93320b7f2bcd302e57f32bdc3a8ad34beb95c5e74a3a6d3dc63/detection 69b3f69e5a2b02338fe6577c62d7bf2e https://www.virustotal.com/#/file/c40dc9c4da50c7bbe85c0c88cc2ee2b98ff44104d1bea87ad01fceb1e485b6cc/detection
Labels:
Fud Pages,
FudPages,
FUDPAGES [.] RU,
fudpages(doit)com,
fudpages@gmail.com,
Phishing,
Phishing Kit
Blackshop Tools - Phishing Kit Author
#BlackshopTools #phishingkit author #threatactoremailblackshop.tools@gmail.com skype blackshop tools ICQ 657940639 sell all Spamming & Hacking tools ---------------Created By blackshop.tools------------------------------ 3b2d31dcd6e2e22af611856644d26e21 https://www.virustotal.com/#/file/fa8cf9cb97931eabd0f10cf3dbe8d8820ffa254df7239ce988d6daba4f91cbe3/detection b9b61c8c84c51c292f4800afef8f56d1 https://www.virustotal.com/#/file/463819bd958981039ed47b6cd7efadb516837f19178bb284c0b5124f6cfb572d/detection dc95ec1097920f11590d8aa9ecea50e6 https://www.virustotal.com/#/file/bf4c4aa938d795d011c5e68261f1edc5a79b2c710175b1bb71426ef12910de27/detection 2749a88067675d74bbf01b7776332082 https://www.virustotal.com/#/file/30e67f21d143ddae4af315daca8745ab7fcf2f08fa73326f42b620728e375de1/detection 0e489a50c0be2b93940f835bb6301736 https://www.virustotal.com/#/file/a5f191da51b09b982412490a1f4bfbe64a491a70c90c3fc4f3f3ee4b51abb697/detection 39ddb4f240c0e837b738f5d7f26ea5b1 https://www.virustotal.com/#/file/da51cb87c17a80201738c76fd51d725ebd5d2035230e9be97615bc9003fbad98/detection
CAZANOVA163 - Phishing Kit Author
#CAZANOVA163 #phishingkit author #threatactoremail
CAZANOVA163-Tools@hotmail.com CAZANOVA163-Free-Tools@hotmail.com a357bcfb2779420c95b5a4a2700ab30a https://www.virustotal.com/#/file/5e7c567e561a59f93db854ac91cd7f933fa1dac2622e9a05906964c9e03935fb/details 63f73f4bc9fc243cb919708286c700d8 https://www.virustotal.com/#/file/06be80d28dd6a0cf906b0e7a24054dce23f0a62c982a1eacb83ffbe7073f8dba/details $headers = "From: CAZANOVA163 <CAZANOVA163-Tools@hotmail.com>\r\n"; $headers = "From: CAZANOVA163 <CAZANOVA163-Free-Tools@hotmail.com>\r\n"; <meta name="description" content="xPayPal_2017 v1.1 | Coded By CaZaNoVa163"> <meta name="author" content="CaZaNoVa163">
Labels:
CAZANOVA163,
CAZANOVA163-Free-Tools@hotmail.com,
CAZANOVA163-Tools@hotmail.com,
Phishing,
Phishing Kit
Anonisma - Phishing Kit Author
#threatactoremail #phishing #phishingkit
Anonisma-Free-Tools@hotmail.com
https://www.virustotal.com/#/file/801806d0cdedfd1ab66ef5b11499df78dcff82c642704bd9d9748c62ccc676d6/detection
https://www.virustotal.com/#/file/3c590a371b79c940d76a3c3a24ccda3a93334ba618d2d2473e61053da349a072/detection
https://www.virustotal.com/#/file/a4d0f7d275d0b04b8b3ff80a58a24991dfd9800d3972027a8dbde6582cb185f5/detection
// Coded By Anonisma ===> 2016 / 2017
include "./includes/lang".$_SESSION['ANONISMA-AYOUB'];
---- | ★ ★ ★ ANONISMA FREE TOOLS ★ ★ ★ | ----
$headers = "From: ANONISMA SMART <Anonisma-Free-Tools@hotmail.com>\r\n";
$text_result_anon .= "|----------| ANONISMA MA DZ TN V3 TEXT RESULT |--------------|\n";
$_SESSION['ANONISMA-AYOUB']="/fr.php";
$_SESSION['ANONISMA-AYOUB']="/es.php";
$_SESSION['ANONISMA-AYOUB']="/it.php";
$_SESSION['ANONISMA-AYOUB']="/ru.php";
$_SESSION['ANONISMA-AYOUB']="/pt.php";
$_SESSION['ANONISMA-AYOUB']="/tr.php";
$_SESSION['ANONISMA-AYOUB']="/pl.php";
$_SESSION['ANONISMA-AYOUB']="/no.php";
$_SESSION['ANONISMA-AYOUB']="/nl.php";
$_SESSION['ANONISMA-AYOUB']="/de.php";
$_SESSION['ANONISMA-AYOUB']="/en.php";
Labels:
Anonisma,
Anonisma Free Tools,
Anonisma-Free-Tools@hotmail.com,
Coded By Anonisma,
Phishing,
Phishing Kit
Wednesday, December 19, 2018
phishingKitTracker.py
# phishing kit parser, used to enrich kit and put into PhishingKitTracker csv format
# @neonprimetime
# https://github.com/neonprimetime/PhishingKitTracker/
import argparse
import zipfile
import urllib.request
from urllib.parse import urlparse
import os
from pathlib import Path
import re
from datetime import date
import hashlib
import shutil
#definitions
class PhishingKitTrackerEntry:
date = date.today().strftime('%m/%d/%Y')
reference = ""
email = ""
emailProvider = ""
mailer = ""
target = ""
domain = ""
zip = ""
threatActor = ""
md5 = ""
url = ""
entries = []
proceed = 1
domain = ""
mailer = ""
filename = ""
md5 = ""
threatActor = ""
itemList = []
isUrls = 0
extractedfoldername = ""
#arguments
arguments = argparse.ArgumentParser("Analyze Phishing Kit, pass 1 url or file to start")
arguments.add_argument("-u", "--url", type=str, required=False, help="Url to a Phishing Kit Zip file")
arguments.add_argument("-f", "--file", type=str, required=False, help="Path to a Phishing Kit Zip file")
arguments.add_argument("-d", "--debug", action="store_true", required=False, help="Enable debugging messages")
arguments.add_argument("-r", "--reference", type=str, required=False, help="Twitter url referencing Phishing Kit")
arguments.add_argument("-l", "--listUrls", type=str, required=False, help="Path to file with a list of Urls to Phishing Kit Zip files in it 1 per line")
arguments.add_argument("-i", "--listFiles", type=str, required=False, help="Path to file with a list of Phishing Kit Zip files 1 per line")
settings = arguments.parse_args()
if(settings.url is None):
if(settings.file is None):
if(settings.listUrls is None):
if(settings.listFiles is None):
if(settings.debug):
print("no url, file, or list param found")
proceed = 0
raise Exception("url (-u) or file (-f) or list (-l,-i) required")
else:
if(settings.debug):
print("list of files param found '{0}'".format(settings.listFiles))
with open(settings.listFiles) as f:
for line in f:
itemList.append(line.rstrip("\r\n"))
else:
if(settings.debug):
print("list of urls param found '{0}'".format(settings.listUrls))
with open(settings.listUrls) as f:
for line in f:
itemList.append(line.rstrip("\r\n"))
isUrls = 1
else:
if(settings.debug):
print("file param found'{0}'".format(settings.file))
itemList.append(settings.file)
else:
if(settings.debug):
print("url param found '{0}'".format(settings.url))
itemList.append(settings.url)
isUrls = 1
#processing
if(proceed == 1):
for item in itemList:
if(isUrls == 0):
filename = item
else:
try:
url = urlparse(item)
domain = url.netloc
filename = os.path.basename(url.path)
if(settings.debug):
print("found domain '{0}'".format(domain))
print("found filename '{0}'".format(filename))
urllib.request.urlretrieve(item, filename)
if(settings.debug):
print("url downloaded '{0}'".format(item))
except:
print("failed to download '{0}'".format(item))
continue
extractedfoldername = str(Path(filename).with_suffix(""))
if(settings.debug):
print("getting file hash for '{0}'".format(filename))
file = open(filename, 'rb')
with file:
md5 = hashlib.md5(file.read()).hexdigest()
if(settings.debug):
print("unzipping file '{0}' to '{1}'".format(filename,extractedfoldername))
with zipfile.ZipFile(filename,'r') as zip_ref:
zip_ref.extractall(extractedfoldername)
if(settings.debug):
print("file unzipped to '{0}'".format(extractedfoldername))
if(settings.debug):
print("starting search for Threat Actor Signatures")
foundActor = 0
for dname, dirs, files in os.walk(extractedfoldername):
if(foundActor == 0):
for fname in files:
fpath = os.path.join(dname, fname)
extension = os.path.splitext(fpath)[1]
if(settings.debug):
print("found file '{0}' with extension '{1}'".format(fpath,extension))
if(extension is not None and extension == ".php"):
if(settings.debug):
print("searching file '{0}'".format(fpath))
with open(fpath) as f:
line = f.read()
match = re.search(r'(?i)(created by|hacked by|coded by|edited by|signed by|made by)([^\r\n\=\+\"\'\,]+)\s+([\,\=\+\"\']|\-\-)', line)
if(match is not None):
threatActor = match.group(1) + match.group(2)
foundActor = 1
break
if(settings.debug):
print("finished search for Threat Actor Signatures")
if(settings.debug):
print("starting search for Threat Actor Emails")
for dname, dirs, files in os.walk(extractedfoldername):
for fname in files:
fpath = os.path.join(dname, fname)
mailer = os.path.basename(fpath)
extension = os.path.splitext(fpath)[1]
if(settings.debug):
print("found file '{0}' with extension '{1}'".format(fpath,extension))
if(extension is not None and extension == ".php"):
if(settings.debug):
print("searching file '{0}'".format(fpath))
with open(fpath) as f:
line = f.read()
matches = re.findall(r'[\w\.-]+@[\w\.-]+', line)
for match in matches:
if(settings.debug):
print("found threat actor email '{0}'".format(match))
entry = PhishingKitTrackerEntry()
if(settings.reference is not None):
entry.reference = settings.reference
entry.email = match
entry.emailProvider = match.split('@')[1].split('.')[0]
entry.mailer = mailer
entry.domain = domain
entry.zip = filename
entry.threatActor = threatActor
entry.md5 = md5
if(isUrls == 1):
entry.url = item
entries.append(entry)
if(settings.debug):
print("deleting zip '{0}'".format(filename))
if(filename is not None and filename != "" and ".zip" in filename):
os.remove(filename)
if(settings.debug):
print("deleting folder '{0}'".format(extractedfoldername))
if(extractedfoldername is not None and extractedfoldername != ""):
shutil.rmtree(extractedfoldername, ignore_errors=True)
if(settings.debug):
print("finished search for Threat Actor Emails")
else:
if(settings.debug):
print("exiting program, proceed={0}".format(str(proceed)))
#output
for entry in entries:
print("{0},{1},{2},{3},{4},{5},{6},{7},{8},{9},{10}".format(entry.date,entry.reference,entry.email,entry.emailProvider,entry.mailer,entry.target,entry.domain,entry.zip,entry.threatActor,entry.md5,entry.url))
# @neonprimetime
# https://github.com/neonprimetime/PhishingKitTracker/
import argparse
import zipfile
import urllib.request
from urllib.parse import urlparse
import os
from pathlib import Path
import re
from datetime import date
import hashlib
import shutil
#definitions
class PhishingKitTrackerEntry:
date = date.today().strftime('%m/%d/%Y')
reference = ""
email = ""
emailProvider = ""
mailer = ""
target = ""
domain = ""
zip = ""
threatActor = ""
md5 = ""
url = ""
entries = []
proceed = 1
domain = ""
mailer = ""
filename = ""
md5 = ""
threatActor = ""
itemList = []
isUrls = 0
extractedfoldername = ""
#arguments
arguments = argparse.ArgumentParser("Analyze Phishing Kit, pass 1 url or file to start")
arguments.add_argument("-u", "--url", type=str, required=False, help="Url to a Phishing Kit Zip file")
arguments.add_argument("-f", "--file", type=str, required=False, help="Path to a Phishing Kit Zip file")
arguments.add_argument("-d", "--debug", action="store_true", required=False, help="Enable debugging messages")
arguments.add_argument("-r", "--reference", type=str, required=False, help="Twitter url referencing Phishing Kit")
arguments.add_argument("-l", "--listUrls", type=str, required=False, help="Path to file with a list of Urls to Phishing Kit Zip files in it 1 per line")
arguments.add_argument("-i", "--listFiles", type=str, required=False, help="Path to file with a list of Phishing Kit Zip files 1 per line")
settings = arguments.parse_args()
if(settings.url is None):
if(settings.file is None):
if(settings.listUrls is None):
if(settings.listFiles is None):
if(settings.debug):
print("no url, file, or list param found")
proceed = 0
raise Exception("url (-u) or file (-f) or list (-l,-i) required")
else:
if(settings.debug):
print("list of files param found '{0}'".format(settings.listFiles))
with open(settings.listFiles) as f:
for line in f:
itemList.append(line.rstrip("\r\n"))
else:
if(settings.debug):
print("list of urls param found '{0}'".format(settings.listUrls))
with open(settings.listUrls) as f:
for line in f:
itemList.append(line.rstrip("\r\n"))
isUrls = 1
else:
if(settings.debug):
print("file param found'{0}'".format(settings.file))
itemList.append(settings.file)
else:
if(settings.debug):
print("url param found '{0}'".format(settings.url))
itemList.append(settings.url)
isUrls = 1
#processing
if(proceed == 1):
for item in itemList:
if(isUrls == 0):
filename = item
else:
try:
url = urlparse(item)
domain = url.netloc
filename = os.path.basename(url.path)
if(settings.debug):
print("found domain '{0}'".format(domain))
print("found filename '{0}'".format(filename))
urllib.request.urlretrieve(item, filename)
if(settings.debug):
print("url downloaded '{0}'".format(item))
except:
print("failed to download '{0}'".format(item))
continue
extractedfoldername = str(Path(filename).with_suffix(""))
if(settings.debug):
print("getting file hash for '{0}'".format(filename))
file = open(filename, 'rb')
with file:
md5 = hashlib.md5(file.read()).hexdigest()
if(settings.debug):
print("unzipping file '{0}' to '{1}'".format(filename,extractedfoldername))
with zipfile.ZipFile(filename,'r') as zip_ref:
zip_ref.extractall(extractedfoldername)
if(settings.debug):
print("file unzipped to '{0}'".format(extractedfoldername))
if(settings.debug):
print("starting search for Threat Actor Signatures")
foundActor = 0
for dname, dirs, files in os.walk(extractedfoldername):
if(foundActor == 0):
for fname in files:
fpath = os.path.join(dname, fname)
extension = os.path.splitext(fpath)[1]
if(settings.debug):
print("found file '{0}' with extension '{1}'".format(fpath,extension))
if(extension is not None and extension == ".php"):
if(settings.debug):
print("searching file '{0}'".format(fpath))
with open(fpath) as f:
line = f.read()
match = re.search(r'(?i)(created by|hacked by|coded by|edited by|signed by|made by)([^\r\n\=\+\"\'\,]+)\s+([\,\=\+\"\']|\-\-)', line)
if(match is not None):
threatActor = match.group(1) + match.group(2)
foundActor = 1
break
if(settings.debug):
print("finished search for Threat Actor Signatures")
if(settings.debug):
print("starting search for Threat Actor Emails")
for dname, dirs, files in os.walk(extractedfoldername):
for fname in files:
fpath = os.path.join(dname, fname)
mailer = os.path.basename(fpath)
extension = os.path.splitext(fpath)[1]
if(settings.debug):
print("found file '{0}' with extension '{1}'".format(fpath,extension))
if(extension is not None and extension == ".php"):
if(settings.debug):
print("searching file '{0}'".format(fpath))
with open(fpath) as f:
line = f.read()
matches = re.findall(r'[\w\.-]+@[\w\.-]+', line)
for match in matches:
if(settings.debug):
print("found threat actor email '{0}'".format(match))
entry = PhishingKitTrackerEntry()
if(settings.reference is not None):
entry.reference = settings.reference
entry.email = match
entry.emailProvider = match.split('@')[1].split('.')[0]
entry.mailer = mailer
entry.domain = domain
entry.zip = filename
entry.threatActor = threatActor
entry.md5 = md5
if(isUrls == 1):
entry.url = item
entries.append(entry)
if(settings.debug):
print("deleting zip '{0}'".format(filename))
if(filename is not None and filename != "" and ".zip" in filename):
os.remove(filename)
if(settings.debug):
print("deleting folder '{0}'".format(extractedfoldername))
if(extractedfoldername is not None and extractedfoldername != ""):
shutil.rmtree(extractedfoldername, ignore_errors=True)
if(settings.debug):
print("finished search for Threat Actor Emails")
else:
if(settings.debug):
print("exiting program, proceed={0}".format(str(proceed)))
#output
for entry in entries:
print("{0},{1},{2},{3},{4},{5},{6},{7},{8},{9},{10}".format(entry.date,entry.reference,entry.email,entry.emailProvider,entry.mailer,entry.target,entry.domain,entry.zip,entry.threatActor,entry.md5,entry.url))
Labels:
Phishing,
Phishing Kit,
PhishingKitTracker,
Python
Wednesday, December 12, 2018
regex extract zip, php, email from grep of phishingkit
after using this grep
https://neonprimetime.blogspot.com/2018/12/grep-recursively-phishing-kit-zip-for.html
in notepad++ you can regex out the zip name, php file name, and email address
replace this
\r\n([^\\]+)\\[^\r]+\\([^\\]+\.php)\:[^\r]+(\"|\')([^\"\'\r]+)(\"|\')[^\r]*
with this
\r\n\1,\2,\4
Monday, December 3, 2018
findstr recursively phishing kit zip for email
after unzipped
findstr /S "@" *.php | findstr "$" | findstr "=" | findstr ";" | findstr "." | findstr /I /V "From" | findstr /I /V "headers" |findstr /I /V "function" | findstr /I /V "key" | findstr /I /V "indexOf" | findstr /I /V "class" | findstr /I /V "isset" | findstr /I /V "@date" | findstr /I /V "server" | findstr /I /V "http" | findstr /I /V "css" | findstr /I /V "style" | findstr /I /V "?" | findstr /I /V "@eval"
Saturday, December 1, 2018
grep recursively phishing kit zip for email
find email
// $send = "bad@bad.com";
grep -r -P '\=\s*.([a-zA-Z][\w\_\.]{5,20})\@([a-zA-Z0-9.-]+)\.([a-zA-Z]{2,4})' | grep -v -P '(?i)(from|headers|array|messsage|find|domain)'
// mail("bad@bad.com", ...)
grep -r -P 'mail\([^\r\n]+\@'
find who created it
// ------ HACKED BY Somebody ----------
grep -r -P "(?i)(Created By|Hacked by|Coded by|Edited By|Signed by|Made by)" * | grep -v function
unzip all files to folder with same name
unzip files to a folder with the same name
>ls
abc.zip
bob.zip
test.zip
>find . -name "*.zip" | while read filename; do unzip -o -d "`basename -s .zip "$filename"`" "$filename"; done;
>ls
abc
abc.zip
bob
bob.zip
test
test.zip
wget -i Urls.txt
download a list of #phishingkit zips
put files into urls.txt
run command
wget -i urls.txt
Friday, November 30, 2018
PhishingKitTracker by neonprimetime
#infosec community
I've recorded the #threatactoremail from each #phishingkit for the last year & started tracking them out on @GitHub to share with you. My hope is this can somehow be used to fight the onslaught of #phishing seen daily
See the list
https://github.com/neonprimetime/PhishingKitTracker/blob/master/PhishingKitTracker.csv
I have 500 phishing kits so far and the data paints some interesting pictures. Such as 82% of the phishing kits I tracked use a @Gmail account to receive the stolen creds. I've also found threat actors that re-use so you can perhaps link together campaigns.
A big thank you, all the credit for the data goes to the #infosec community on twitter that hunts and finds all the evil #phishing sites such as @TechHelpListCom @IpNigh @ANeilan @leunammejii @ActorExpose @n0p1shing @dave_daves @FewAtoms @nullcookies @PhishingAi@jcybersec_ @JonSelman @MaelSecurity @demonslay335 @dms1899 @malware_traffic @olihough86 @packet_Wire @ps66uk @Ring0x0 @sS55752750 @teoseller @tiketiketikeke @ViriBack @WifiRumHam @PhishTank_Bot and everyone else in the community
If anybody knows people @Gmail , @Yandex, @Yahoo, @Zoho, @ProtonMail that care about this type of data and could perhaps help the #infosec community start streamline reporting or detection of these email accounts that receive stolen creds daily that's be sweet.
If anybody knows a better place to upload zipped up phishing kits than VT , I'd love to be sharing and archiving them somewhere the whole community has access to.
If anybody every has #phishing threat actor emails they wanted appended to this list just CC me and I'll do my best to get them added
If anybody has suggestions on better ways to do this & share w/ the community, extra data/fields to track, etc. I'm all open ears, for example if somebody wanted to build a tracker website for the community to use you'd be my hero ! Otherwise, HAPPY FRIDAY
https://github.com/neonprimetime/PhishingKitTracker/blob/master/PhishingKitTracker.csv
I have 500 phishing kits so far and the data paints some interesting pictures. Such as 82% of the phishing kits I tracked use a @Gmail account to receive the stolen creds. I've also found threat actors that re-use so you can perhaps link together campaigns.
A big thank you, all the credit for the data goes to the #infosec community on twitter that hunts and finds all the evil #phishing sites such as @TechHelpListCom @IpNigh @ANeilan @leunammejii @ActorExpose @n0p1shing @dave_daves @FewAtoms @nullcookies @PhishingAi@jcybersec_ @JonSelman @MaelSecurity @demonslay335 @dms1899 @malware_traffic @olihough86 @packet_Wire @ps66uk @Ring0x0 @sS55752750 @teoseller @tiketiketikeke @ViriBack @WifiRumHam @PhishTank_Bot and everyone else in the community
If anybody knows people @Gmail , @Yandex, @Yahoo, @Zoho, @ProtonMail that care about this type of data and could perhaps help the #infosec community start streamline reporting or detection of these email accounts that receive stolen creds daily that's be sweet.
If anybody knows a better place to upload zipped up phishing kits than VT , I'd love to be sharing and archiving them somewhere the whole community has access to.
If anybody every has #phishing threat actor emails they wanted appended to this list just CC me and I'll do my best to get them added
If anybody has suggestions on better ways to do this & share w/ the community, extra data/fields to track, etc. I'm all open ears, for example if somebody wanted to build a tracker website for the community to use you'd be my hero ! Otherwise, HAPPY FRIDAY
Labels:
Github,
Phishing,
Phishing Kit,
PhishingKitTracker,
threatactoremail
Sunday, November 25, 2018
#phishingkit 10/2017 to 11/26/2018 from Twitter
This summary is not available. Please
click here to view the post.
Subscribe to:
Posts (Atom)