simple windows command to find group policy passwords in xml
findstr /SI cpassword \\DC\sysvol\DOMAIN\Policies\*.xml
e.g. Groups.xml contains cpassword
Thursday, May 16, 2019
Find Group Policy Passwords
Labels:
cpassword,
gpo,
group policy,
groups.xml,
password
Friday, May 10, 2019
New PhishingKitTracker Blog
Just a heads up I'm moving all my PhishingKitTracker blog posts ( @PhishKitTracker - https://github.com/neonprimetime/PhishingKitTracker ) over to this new blog url
https://phishingkittracker.blogspot.com/
This blog ( @neonprimetime ) will continue to be for #malware and other #infosec topics
https://phishingkittracker.blogspot.com/
This blog ( @neonprimetime ) will continue to be for #malware and other #infosec topics
Tuesday, May 7, 2019
IzLaden - Phishing Kit Author
#izladen #phishingkit author #threatactoremail izladen-Free-Tools@hotmail.com ---- | ★ ★ ★ IzlAden BenGazi FREE TOOLS ★ ★ ★ | ---- |----------| IzlAden BenGazi V3 TEXT RESULT |--------------| Coded By IzlAden BenGazi ===> 2016 / 2017 227ce240dff32a0a35810b0040539ae2 https://www.virustotal.com/#/file/735a16f31af8159af71c40738a22c5638d41bd58144014b9a3fee00390a1da6b/details a9fd8300c7a5654f1ee9247ebdb3e42a https://www.virustotal.com/#/file/7434db52972fd2aa7f253bded2efff92f6069fd9e8ff7beb27c5d998ce803c41/detection c37d8e468a67748c7f9687ecfe39c960 https://www.virustotal.com/#/file/4e1ce76c96c3163d1da5060157b4c0924647e4938843f827f36380837bb7610e/detection
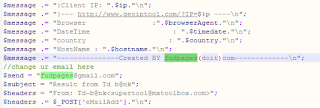
FudPages - Phishing Kit Author
#fudpages #phishingkit author #threatactoremail fudpages@gmail.com ---------------Created BY fudpages(doit)com------------- ---------------Created BY fudpages------------- ----------- FUDPAGES [.] RU -------------- abc845784335374ecb86cc7d9f105ba7 https://www.virustotal.com/#/file/3e76cff314a6b4fef91784f8fab3f21e985f68bd9aa909cdca0245611a3f8757/detection 070a0ebacac551e86ed00e1118f9a969 https://www.virustotal.com/#/file/bcb77cbee636b93320b7f2bcd302e57f32bdc3a8ad34beb95c5e74a3a6d3dc63/detection 69b3f69e5a2b02338fe6577c62d7bf2e https://www.virustotal.com/#/file/c40dc9c4da50c7bbe85c0c88cc2ee2b98ff44104d1bea87ad01fceb1e485b6cc/detection
Labels:
Fud Pages,
FudPages,
FUDPAGES [.] RU,
fudpages(doit)com,
fudpages@gmail.com,
Phishing,
Phishing Kit
Blackshop Tools - Phishing Kit Author
#BlackshopTools #phishingkit author #threatactoremailblackshop.tools@gmail.com skype blackshop tools ICQ 657940639 sell all Spamming & Hacking tools ---------------Created By blackshop.tools------------------------------ 3b2d31dcd6e2e22af611856644d26e21 https://www.virustotal.com/#/file/fa8cf9cb97931eabd0f10cf3dbe8d8820ffa254df7239ce988d6daba4f91cbe3/detection b9b61c8c84c51c292f4800afef8f56d1 https://www.virustotal.com/#/file/463819bd958981039ed47b6cd7efadb516837f19178bb284c0b5124f6cfb572d/detection dc95ec1097920f11590d8aa9ecea50e6 https://www.virustotal.com/#/file/bf4c4aa938d795d011c5e68261f1edc5a79b2c710175b1bb71426ef12910de27/detection 2749a88067675d74bbf01b7776332082 https://www.virustotal.com/#/file/30e67f21d143ddae4af315daca8745ab7fcf2f08fa73326f42b620728e375de1/detection 0e489a50c0be2b93940f835bb6301736 https://www.virustotal.com/#/file/a5f191da51b09b982412490a1f4bfbe64a491a70c90c3fc4f3f3ee4b51abb697/detection 39ddb4f240c0e837b738f5d7f26ea5b1 https://www.virustotal.com/#/file/da51cb87c17a80201738c76fd51d725ebd5d2035230e9be97615bc9003fbad98/detection
CAZANOVA163 - Phishing Kit Author
#CAZANOVA163 #phishingkit author #threatactoremail
CAZANOVA163-Tools@hotmail.com CAZANOVA163-Free-Tools@hotmail.com a357bcfb2779420c95b5a4a2700ab30a https://www.virustotal.com/#/file/5e7c567e561a59f93db854ac91cd7f933fa1dac2622e9a05906964c9e03935fb/details 63f73f4bc9fc243cb919708286c700d8 https://www.virustotal.com/#/file/06be80d28dd6a0cf906b0e7a24054dce23f0a62c982a1eacb83ffbe7073f8dba/details $headers = "From: CAZANOVA163 <CAZANOVA163-Tools@hotmail.com>\r\n"; $headers = "From: CAZANOVA163 <CAZANOVA163-Free-Tools@hotmail.com>\r\n"; <meta name="description" content="xPayPal_2017 v1.1 | Coded By CaZaNoVa163"> <meta name="author" content="CaZaNoVa163">
Labels:
CAZANOVA163,
CAZANOVA163-Free-Tools@hotmail.com,
CAZANOVA163-Tools@hotmail.com,
Phishing,
Phishing Kit
Anonisma - Phishing Kit Author
#threatactoremail #phishing #phishingkit
Anonisma-Free-Tools@hotmail.com
https://www.virustotal.com/#/file/801806d0cdedfd1ab66ef5b11499df78dcff82c642704bd9d9748c62ccc676d6/detection
https://www.virustotal.com/#/file/3c590a371b79c940d76a3c3a24ccda3a93334ba618d2d2473e61053da349a072/detection
https://www.virustotal.com/#/file/a4d0f7d275d0b04b8b3ff80a58a24991dfd9800d3972027a8dbde6582cb185f5/detection
// Coded By Anonisma ===> 2016 / 2017
include "./includes/lang".$_SESSION['ANONISMA-AYOUB'];
---- | ★ ★ ★ ANONISMA FREE TOOLS ★ ★ ★ | ----
$headers = "From: ANONISMA SMART <Anonisma-Free-Tools@hotmail.com>\r\n";
$text_result_anon .= "|----------| ANONISMA MA DZ TN V3 TEXT RESULT |--------------|\n";
$_SESSION['ANONISMA-AYOUB']="/fr.php";
$_SESSION['ANONISMA-AYOUB']="/es.php";
$_SESSION['ANONISMA-AYOUB']="/it.php";
$_SESSION['ANONISMA-AYOUB']="/ru.php";
$_SESSION['ANONISMA-AYOUB']="/pt.php";
$_SESSION['ANONISMA-AYOUB']="/tr.php";
$_SESSION['ANONISMA-AYOUB']="/pl.php";
$_SESSION['ANONISMA-AYOUB']="/no.php";
$_SESSION['ANONISMA-AYOUB']="/nl.php";
$_SESSION['ANONISMA-AYOUB']="/de.php";
$_SESSION['ANONISMA-AYOUB']="/en.php";
Labels:
Anonisma,
Anonisma Free Tools,
Anonisma-Free-Tools@hotmail.com,
Coded By Anonisma,
Phishing,
Phishing Kit
Friday, May 3, 2019
Wireshark Fix for Error No Protocol Specified
Working through a pen testing lab, was getting access denied when trying to capture.
Tried running sudo and it doesn't let you cause it's a security risk.
But when we're in a pen test lab, i'm ok with that risk.
But I was still getting this error "no protocol specified"
> sudo wireshark
No protocol specified
No protocol specified
(wireshark:3962): Gtk-WARNING **: cannot open display: :0.0
The fix I found
> export XAUTHORITY=/home/mooreted/.Xauthority
> sudo wireshark
Labels:
.Xauthority,
error,
no protocol specified,
Wireshark,
XAuthority
Wednesday, May 1, 2019
Registry Explorer basic usage
Open up a registry hive such as
c:\windows\system32\config\SOFTWARE
with Registry Explorer from Eric Zimmerman
https://ericzimmerman.github.io/#!index.md
to view registry contents
c:\windows\system32\config\SOFTWARE
with Registry Explorer from Eric Zimmerman
https://ericzimmerman.github.io/#!index.md
to view registry contents
Labels:
eric zimmerman,
hive,
regcmd,
Registry,
registryexplorer
Date Time Conversions with DCode
If you have a date/time in numerical format such as in the registry
SOFTWARE\Microsoft\Windows NT\CurrentVersion\InstallDate
1510798682
Use the software DCode with the format: "Unix:Numeric Value" to get the actual date 11/16/2017
https://www.digital-detective.net/dcode/
Subscribe to:
Comments (Atom)