Normally on an non-obfuscated phishing kit you can find a threat actor's email address by just viewing it like this.
But in a few instances I ran across php mailer files that looked like this
And if I used Notepad++ JSTool -> JSFormat and beautified it a bit I see the php mail call, but it's all obfuscated and there is no clear email address.
In order to find the email address I attempted the following. I searched for either the '@' symbol or for \x40 (which is the hex equivalent of the '@' symbol). Why? because my thought was I'm looking for an email address so it's gotta contain that character. I ended up finding it a line or so above the mail call.
So I pulled out that obfuscated php code.
["b\x71m\x73\x63\x70\x74\x68\x6b\x69a"]
} = "Fr\x6f\x6d: \x56\x61\x69\x72us O\x2e\x3c\x75\x70\x64\x61\x74\x65s@\x6f\x75\x72t\x69\x6de\x77\x68o\x72\x65\x72s.\x63\x6fm\x3e";
All I really care about is the value (the right hand side of the equal '=' sign.
"Fr\x6f\x6d: \x56\x61\x69\x72us O\x2e\x3c\x75\x70\x64\x61\x74\x65s@\x6f\x75\x72t\x69\x6de\x77\x68o\x72\x65\x72s.\x63\x6fm\x3e";
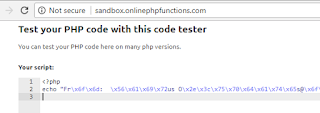
Then I find an online php sandbox such as
http://sandbox.onlinephpfunctions.com/
I tweak the code slighly to 'echo' or print out the contents
<?php
echo "Fr\x6f\x6d: \x56\x61\x69\x72us O\x2e\x3c\x75\x70\x64\x61\x74\x65s@\x6f\x75\x72t\x69\x6de\x77\x68o\x72\x65\x72s.\x63\x6fm\x3e";
Paste that modified code into the sandbox
And view the results
In this case it says
From: Vairus O.<updates@ourtimewhorers.com>
This was a failed attempt because that ends up being the from line of the email but not the "to" or "recipient". So I have to go back and try again.
If I read a bit more about php mail function ( http://php.net/manual/en/function.mail.php ) I realize that the $to parameter is the first one, so what I need to do is look specifically at that first parameter and see what it's getting filled with.
This code
mail($ {
$ {
"G\x4c\x4f\x42\x41\x4c\x53"
}
["\x6b\x74\x77\x7a\x62y\x78z"]
},
And more specifically this code (you can ignore many of the curly brackets as they're just there for confusion.
"G\x4c\x4f\x42\x41\x4c\x53"["\x6b\x74\x77\x7a\x62y\x78z"]
Now if you find a hex to ascii converter online such as this one ( https://www.rapidtables.com/convert/number/hex-to-ascii.html )
You can uncover that this deobfuscates to
GLOBALS["ktwzbyxz"]
Which GLOBALS is apparently a way to access global variables from anywhere in php
So we need to uncover what is in the global variable "ktwzbyxz"
Since the attacker seems to go back and forth between ascii and hex characters, i just search in the file for the first 2 characters of the global variable
\x6b\x74
And I get a hit higher up in the file
$ {
"\x47L\x4f\x42A\x4cS"
}
["\x6b\x74\x77\x7a\x62\x79\x78\x7a"] = "\x73end";
$ {
"\x47\x4c\x4f\x42A\x4c\x53"
}
That appears after de-obufscating to be the attacker setting
GLOBALS["ktwzbyxz"] = "send"
Oh well, so I tried :-) It does not appear that this obfuscated phishing kit has the threat actor's email address in it yet. Either I'm missing something (which is possible cause I'm still learning) or this is meant to be set somewhere somehow but the threat actor after they purchase the phishing kit and extract the zip, in which case this is just the template and it doesn't include it yet.
Thanks for taking the time to read through this.